
How to Code a Network Scanner to See If Anyone Is Camping-out on Your Wi-Fi
A nice technical definition would say…
ARP is the Address Resolution Protocol, used to translate between Layer 2 MAC addresses and Layer 3 IP addresses. ARP resolves IPs to MAC addresses by asking, “Who has IP address 192.168.2.140, tell me.” An example of an ARP reply is “192.168.2.140 is at 00:0c:29:69:19:66.” -CISSP Study Guide (Third Edition)
Put another way, ARP operates by just using requests and responses. Simply stated, your computer asks (request) all the other devices using the same Wi-Fi network to send (response) their MAC address. Here’s an illustration that might help from The Illustrated Network by Walter Goralski:
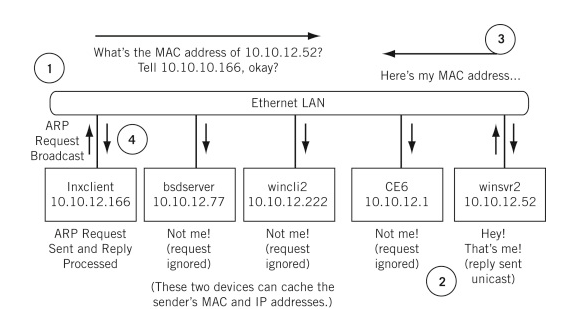
Scapy is a python program used for network administration tasks, such as network scanning.
arping() is just the Scapy built-in function used to initiate the protocol to scan the network.
I would say awareness is number one! Being able to scan your networks will enable you to respond to potential threats much quicker, and therefore mitigating risk and damage.
Another solution I came across, but I haven’t personally done, suggested that “secure networks should consider hard-coding ARP entries.” That advice also came from the CISSP Study Guide (Third Edition).
Here’s some python code that uses Scapy to scan the devices on your Wi-Fi network. It’s super short and simple and really nothing to brag about. However, I think the simplest tools are the best.
Here’s the code:
#!/usr/bin/env python
import scapy.all as scpy
def scan(ip):
scpy.arping(ip)
scan("xxx.xxx.xxx.x/xx")
I’ve tested this code on Linux with success. It should work on Mac and Windows because Scapy works on all operating systems, but you might have to refactor it. To use it, you’ll just replace the x’s with your IP address. If you don’t know your IP address then you might be able to use 192.168.0.1 or 192.168.157.1, because these are common default values on LANs. If not, find out your IP by running the following command in your command prompt:
route -n for Linux/Mac
route PRINT for Windows
This command will show you your IP. It will be under the column titled “Gateway”

When you have your IP address, you can run the network scanning code and the output for that should look like:
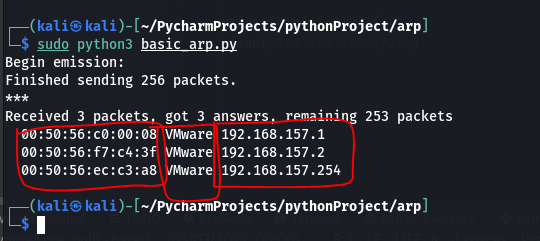
When the program is done running, it will spit out three columns for you. From left to right: MAC address, device name/manufacturer, IP address.
So with this output, I can see there are no unfamiliar devices and now I have a little bit more peace of mind that I’m not being spied on. Of course, there are other measures a malicious hacker can take to be more undetectable but that gets into more advanced covert tactics which creates more work for the typical lazy hacker to do. The important takeaway here is learning how to gain more awareness of your network in order to respond to threats sooner.
I hoped you enjoyed this info and that you found it useful. For further reading:
https://www.sciencedirect.com/topics/computer-science/address-resolution
Hasta la pasta, amigos!
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!