
Mobile Device Security

I’m summarizing the CompTIA certification because it is one of the more widely recognized certifications amongst employers.
To learn more about the certification I recommend searching the official CompTIA website because I’m just going to jump into the study material, right meow!
When it comes to IT security a balancing act takes place between security and convenience. These two aspects inversely correlate with each other, meaning when one favors more security, then convenience is sacrificed and vice versa. Furthermore, that convenience relates to the ease of access regarding a company’s data and/or network.
These security measures can be generally split into two categories: Information Security and Information Systems Security.
This refers to the security of the data being held within a system, not the systems themselves. For example, bank balances or a list of client emails.
More formally,
It is the act of protecting data and information from unauthorized access, unlawful modification and disruption, disclosure, corruption and destruction.
This refers to the security of devices (systems) that hold the data, or…
The act of protecting the systems that hold and process our critical data.
The following paragraphs will cover the basic topics that comprise good security as well as other fundamental areas of knowledge to be an effective professional.
In order to lay the foundation for good InfoSec practices, one must know some important concepts. These are a couple of acronyms that are pretty easy to memorize.
Imagine that you want to protect your Data & Information with an imaginary triangle. Obviously, this triangle will be comprised of three sides, those being:
Authentication
The first ‘A’ refers to authentication. With this, we’re making sure that a person’s identity is established with proof and confirmed by a system. Logging into an account with a username and password is an example of this. But authentication can be beefed-up by incorporating more practices, which include:
As you might imagine, it would be cumbersome to implement all of the above practices for authentication. The number of practices implemented should be relative to the importance/sensitivity of the data being protected. However, this provides a good demonstration of the constant conflict between Security and Convenience, as described earlier.
Authorization
Occurs when a user is given access to a certain piece of data or certain areas of a building, like when having a badge to access a special department.
Accounting
Refers to the tracking of data, computer usage, and network resources. Also, this allows for non-repudiation, which occurs when you have proof that someone has taken an action. Log files help ensure good accounting practices
This covers the avenues of attack through which an attacker can take. They include:
To be most effective at staving off attacks, it is best practice to implement the following three controls in combination. These controls include:
Hackers are generally categorized by their ethics and skill level. To describe a hackers ethics we have four descriptive terms:
To describe a hacker’s skill level we just say a white hat hacker, for example, to refer to a moderately skilled hacker. However, to describe a highly skilled hacker we would say an elite white hat hacker. Elites are typically characterized as
hackers that can find and exploit vulnerabilities before anyone else does. 1 in 10,000 are elite.
On the lower end of the skill level spectrum, we have Script Kiddies. They are the opposite of elite and have limited skills. They are typically only capable of running other people’s exploits and tools because they are not savvy enough to create their own.
These are the 'meanies' that conduct malicious attacks. There are four general categories and they’ll be listed below in order from least dangerous to most dangerous.
Script kiddies — as we saw above, this group of threat actors is not very skilled, furthermore, script kiddies typically don’t operate ethically which is why they are their own category of threat actors; most of these types don’t even know about the tools they use; a.k.a. baby hackers and the least dangerous, but dangerous nonetheless!
Hacktivists — hackers who are driven by a cause like social change, political agendas, or terrorism; like the hacker group Anonymous
Organized Crime — hackers who are part of a crime group that is well-funded and highly sophisticated; these types use ransomware the most
Advanced Persistent Threats (APTs) — highly trained and funded groups of hackers (often by nation-states) with covert and open-source intelligence at their disposal
Threat intelligence refers to the information you have on an attack or potential threat, and the sources of that information. These aspects are very important to factor because they help us gauge the reliability of the intelligence and source, and therefore our response to the attack or potential threat. We can think of threat intelligence as having various properties. Those properties include:
So, not only are there several properties of intelligence, but also a few types of sources of intelligence. They include:
A list of open-source data includes:
Lastly, we have Open-Source Intelligence (a.k.a. OSINT), and this refers to methods of obtaining information about a person or organization through public records, websites, and social media. This would include google searches and facebook searches.
Furthermore, there’s one more distinction we need to make regarding threat intelligence. That is explicit vs. implicit knowledge. Explicit knowledge refers to the knowledge gained from harvesting one of the above-mentioned data sources. Implicit knowledge refers to knowledge gained from experience or working within a niche domain, and even intuition.
This cyber security technique aims at detecting threats that have not been discovered by normal security monitoring. This is a proactive approach, as opposed to the typical reactive approach commonly taken. It’s important to realize that this is not like pentesting because it only involves using data that is already available. As a result, threat hunting has the advantage of being less disruptive to business operations than pentesting.
In the threat hunting process, we Establish a Hypothesis. We derive a hypothesis from threat modeling and is based on potential events with higher likelihood and higher impact. When we consider our hypothesis, we ask the questions:
In addition, we’ll Profile Threat Actors and Activities, which involves the creation of a scenario that shows how a prospective attacker might attempt an intrusion and what their objectives might be.
Threat hunting relies on the usage of the tools developed for regular security monitoring and incident response. This will involve looking at the file logs, system process information, file system registry changes, etc… These items are typically viewed within a SIEM (Security Information & Event Management system), which is like a dashboard of charts. Furthermore, the network traffic, executable process list, and other infected hosts are analyzed. Then we’ll attempt to identify how the hypothesized malicious process was executed.
While threat hunting has the benefit of being less disruptive than pentesting, it does consume a lot of resources and time to conduct. However, it can yield several benefits, such as:
Overall, the main result is that a company’s targets are harder for adversaries to access.
These are models of thinking developed by those trying to protect their assets and aid in the Threat Hunting process. They provide a framework by which to basically conduct a thought experiment in order to anticipate the steps and stages a malicious hacker might do to conduct an intrusion and exfiltrate data.
There are three frameworks commonly used. They can be used separately, but it has been found that when all three are combined anticipating the attacks can be more efficient or accurate.
The three frameworks include Kill Chain Analysis, MITRE ATT&CK framework, and the Diamond Model of Intrusion Analysis. Below each will be summarized.
Lockheed Martin developed this model and it describes the stages by which a threat actor progresses a network intrusion. This is the oldest of the frameworks used. It is often criticized for being too linear, instead of iterative. It is further criticized for focusing on just perimeter security → an outside-in approach to a network intrusion, which can overlook the need to have internal security measures in the event of a perimeter security breach.
Regardless of the shortcomings, it is still a useful framework to mentally map out how an intrusion would take place. The stages are as follows:
One benefit of going through this lengthy thought process is that it can be used to define a defensive course-of-action matrix to counter progress at each stage of the attack. A security professional can use this to anticipate what an attacker might do. For example, what breadcrumbs to look for at each step, what programs/software the attacker might use, how attackers might defend themselves, what might be the attackers' motives, etc…
This is a knowledge base maintained by the MITRE Corporation. It lists and explains specific adversary tactics, techniques, and common knowledge or procedures (attack.mitre.org). This is quite a neat tool and the website is very efficiently organized for easy navigation.
It provides a framework with which to address multiple lines of attack, and so it is more of a matrix type of model. The pre-ATT&CK tactics matrix aligns with the reconnaissance and weaponization phases of the kill chain.
A framework for analyzing cybersecurity incidents and intrusions by exploring the relationships between four core features: adversary, capability, infrastructure, and victim.
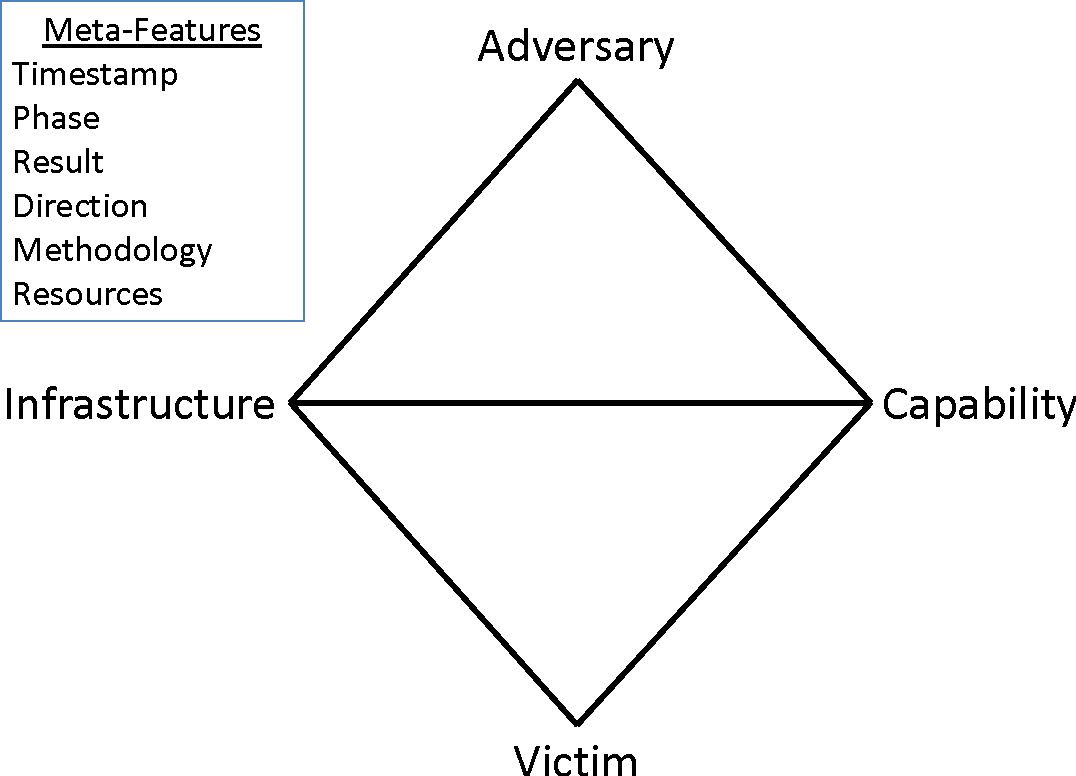
Furthermore, there’s a list of meta-features to be considered in tandem with the model. So, by applying this framework, an example thought process would go as follows:
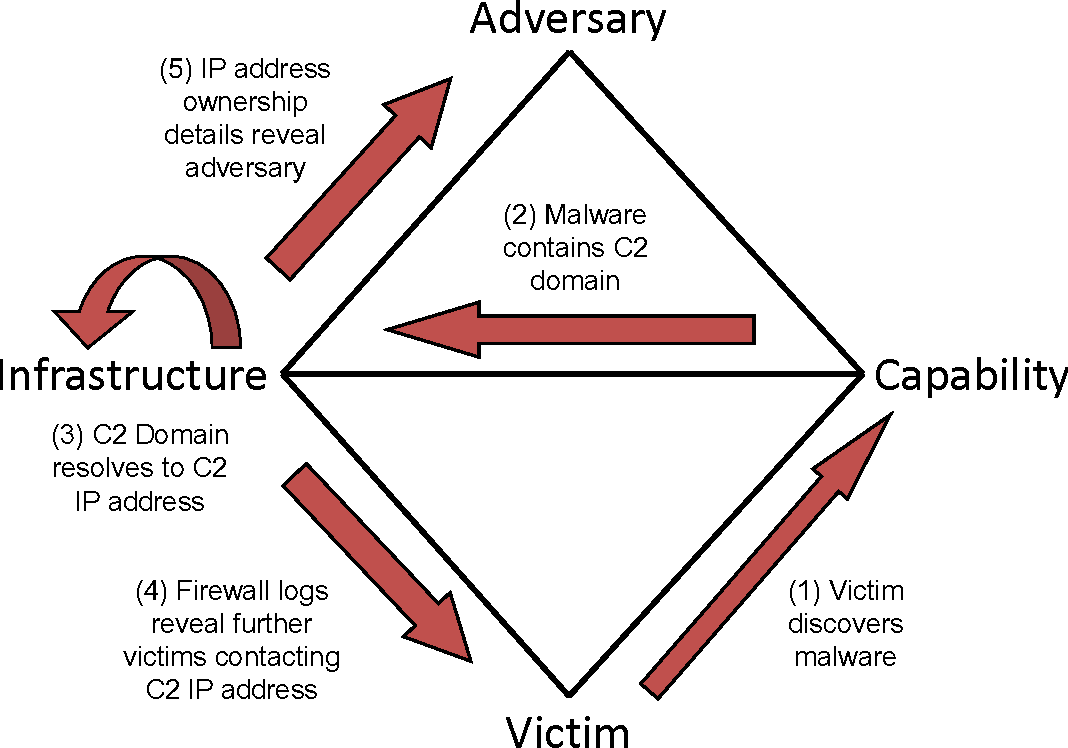
Essentially, map out each past incident, or hypothetical incident, to the diamond model above and determine the flow of the attack. After applying this framework, a security professional will create a tuple containing an array of information gleaned from this process for storage and further analysis.
That’s all folks!
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!