
Can I use penicillin on my malware infection?

Merely knowing how hackers do this will decrease the likeliness of this attack happening to you. Awareness is much more powerful than people give it credit.
In this article I will humbly attempt to describe how a hacker uses DNS Spoofing. In a future article, I’ll share how to detect this kind of a attack to protect yourself even more.
This can be relatively involved in terms of setting up everything in order to conduct this type of attack, so I guess you can take some comfort in also knowing that this isn’t the easiest thing to do for most people.
This is essentially the first step before doing the actual spoofing. To spoof, one must achieve the position of “man in the middle” within a network please refer to the crude illustration below. The person circled in red has attained the m.i.t.m. position

After attaining the m.i.t.m. position within the network, the malicious hacker can start intercepting packets from you and your router. As these packets are being intercepted they are being stashed in a queue. This is done to control the flow of packets and allow the hacker to modify them.
However, the hacker will let most of the packets flow through unmodified. For this type of attack, the hacker only needs to modify the packets coming from the Router to the User. This is how the hacker can change what you see and is highlighted red in the crudely drawn illustration below

Are there obvious signs on a website that it has been spoofed?

To change what you see, they will modify the rdata field, found within the \an \ layer of the packet. Circled in red below

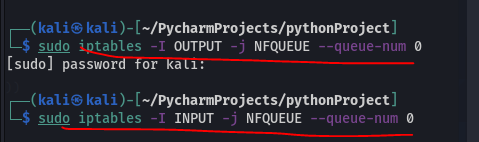
Create the queues that will capture the packets flowing between the User and the Router. Commands underlined in red below:
Run a DNS Spoofing program, like the one below:
#!usr/bin/env python import netfilterqueue import scapy.all as scapydef process_packet(packet): scapy_packet = scapy.IP(packet.get_payload()) print(scapy_packet.show()) packet.accept()queue = netfilterqueue.NetfilterQueue() queue.bind(0, process_packet) queue.run()
The above python program can’t actually modify the packets, but when you run it, it will show packet information.
Modify the packet. Like I mentioned, the program above won’t modify any info, but that is the last step to DNS spoofing.
The website I used in the examples above is one that I’m developing for a company. They granted me permission to use their website for these educational screenshots.
I hope this helps provide you with more situational awareness in your digital life. Read Part Deux to learn more.
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!