
Mobile Device Security

Good cybersecurity is holistic, especially when you incorporate a defense-in-depth strategy. Every angle must be considered and this means the task of securing our digital assets spills over into the physical realm. In the following sections we’ll explore how to best support digital operations with facility design.
By facility design, I mean the fire suppression systems, HVAC, and shielding against EMPs. However, because of advances in technology, vehicles are starting to become extensions of networks. With that in mind we’ll cover vehicular vulnerabilities also.
To clarify, some of these measures can be seen as mundane operations management, and easy to overlook since they can seem so ‘basic.’ Anyway, these measures seek to do more than just address risks from human threat actors, but they also address risks caused by natural disasters or unfortunate mistakes and whatnot. It is helpful to remember the CIA Triad, which is the goal of ensuring Confidentiality, Integrity & Availability of data within an organization’s network. The facility design measures we will cover help with this goal.
Process of controlling and/or extinguishing fires to protect an organization’s employees, data, and physical property. Obviously, it’s important to ensure the safety of not only the network and data within a company, but its employees as well.
There are three types of fire suppression systems: handheld(fire extinguishers), sprinklers and special hazard protection.
Not all fires are created equal. There are actually several classes of fire depending on the fuel of the fire. CompTIA labels these as class A, B, C, D, and K. I found variations of this classification system upon research, which is why I specify that “CompTIA labels these…”
Class A fires burn from ordinary combustibles, such as wood, paper, rubber, fabrics and many plastics. Water is good enough to put these out.
Class B refers to fires fueled by flammable liquids and gases, such as gasoline, oils, paint, lacquer, tar, hydrogen, oxygen, methane…
Class C fires come from live electrical equipment. Many times, the best way to put these out is by turning off the electricity… but get the extinguisher regardless. CO2-based or dry powder extinguisher recommended.
Class D fires are started by combustible metals or metal alloys, like potassium, magnesium, titanium, lithium and some others. Most laptops use lithium batteries so having an extinguisher for this type of fire is important for any office. Use dry powder or CO2 based extinguisher. Actually, just have both types available.
Lastly, there are Class K fires. These are basically kitchen fires, which are typically started by combustible cooking media, such as vegetable/animal fats/oils.
In terms of fire extinguishers, there are several types, but we’ll just cover three:
Why not collect ’em all?!?!

Wet pipe sprinkler systems have their pipes filled with water all the way to the sprinkler head and just wait for the bulb to burst or melt. When activated the water smothers the fire and reduces the heat.
Dry pipe sprinkler systems filled with pressurized air and only push water into the pipes when needed to combat fire. These are for use in colder regions so there’s no threat of the pipes bursting if it gets too cold.
A pre-action sprinkler system is similar to a dry pipe system but will activate when just heat or smoke is detected. No flames required for activation.
So sprinklers are super effective at putting out fires, but we don’t necessarily want to use sprinklers in a server room. If these sprinklers are activated by accident then it would damage everything in the server room for nothing.
To avoid this, people use a Clean Agent System. This fire suppression system relies upon gas to suffocate the fire (HALON, FM-200, or CO2) instead of water.
… but if you hear a loud alarm in the server room… GET OUT! If the clean agent system is activated and you’re still in the room then the fire won’t be the only thing that gets suffocated because all of the oxygen will be displaced in that room.
This fun acronym stands for Heating, Ventilation, and Air Conditioning. It may appear unrelated to electrical systems but this banal aspect of facility design is important for computers because they produce a lot of heat. For proper functioning, a facility’s HVAC system must be designed to displace this heat.
Furthermore, it also needs to control the humidity.
The happy range for humidity is around 40%.
A common practice in server room design is to arrange the server racks to have alternating hot and cold aisles. This allows for efficient dissipation of excess heat. Refer to the image below:
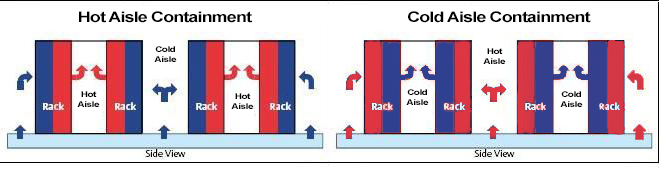
Cold air will flow in to the cold aisles and hot air will flow out in the hot aisles. The cold aisles will also be the ‘working aisles’ for employees, for the most part, hopefully.
HVAC systems may be connected to ICS and SCADA networks. We’ll cover these in more detail later in the article. With regards to HVAC systems, though, they provide a means for a remote operator to control temperature and humidity or address a power outage.
This is the way we secure our network media, a.k.a. the cables! Shielded Twisted Pair (STP) adds a layer of shielding inside the cable by adding a layer of foil within the cable.
The foil blocks electromagnetic interference (EMI) and radio frequency interference, and keeps the cables from leaking out data. These STP cables are more expensive than regular cables.
Fun fact, HVAC systems also need to be shielded because they can generate their own EMI. This can also interfere with networks, too.
Shielding installed around an entire room that prevents electromagnetic energy and radio frequencies from entering or leaving the room. Not commonly applied. Typically, we only see government facilities and paranoid billionaires incorporating this into their security posture.
BONUS TIP: Your microwave appliance is an actual faraday cage. If you feel like your phone is listening to you then put it in the microwave. DON’T TURN ON THE MICROWAVE. Just close the door, and then you’re good. Your friends and family may think you’re crazy, but they just don’t understand Defense-in-depth.
On the topic of government entities, the U.S. government does have a standard for the level of shielding required in a building to ensure emissions and interference cannot enter or exit the facility. They have been dubbed TEMPEST facilities.
TEMPEST facilities are also resistant to EMPs (electromagnetic pulses) which is pretty neat. Remember how they use EMPs to fight the machines in the Matrix movies? Anyway, not relevant, that was just a tangential question that popped up in my head.
This refers to any vehicle integrated with computers. That’s basically most cars built in the 90’s or newer, and really any vehicle with electrical wiring. Vehicles connect numerous subsystems over a controller area network (CAN). Examples of these subsystems include your cruise control, check engine light, steering, and so on.
Controller Area Network (CAN)
Attach the exploit to OBD-II — think of a hacker disguised as a valet plugging a tracking device into your OBD-II plug
Exploit over onboard cellular — prevented by having two separate systems, one for the CAN and the other for the cellular connection
Exploit over onboard Wi-Fi — if someone is close enough to your vehicle
This CAN system was integrated into cars when they were completed isolated from external networks so cybersecurity wasn’t top priority. That’s changing now, because these CAN systems are incorporating cellular and Wi-Fi networks which increases risk exposure.
Read this article, if you wish to be further concerned with cars that have computers in them.
Internet of Things (IoT) is a group of objects (electronic or not) that are connected to the wider Internet by using embedded electronic components. This can just about be anything. Some useful examples include smart door locks, security systems, smart TVs, wi-fi enable lightbulbs, and the list goes on
Most smart devices use an embedded version of Linux or Android as their OS.
Unfortunately, convenience is often prioritized over security when developing IoT devices. Because of this, devices must be secured and updated when new vulnerabilities are found.
More IoT devices = more attack vectors. Be sure to properly install, secure and segment these devices when incorporating them into your network. IoT devices have become common pivot points for gaining privileged access so be wary.
A computer system that is designed to perform a specific, dedicated function. These are common for manufacturing or automated processes, for example, a microcontroller for a medical drip.
Embedded systems are considered static environments where frequent changes are not made or allowed. They’re stripped down and mostly made to do just one task, like flow rate monitoring. However they can be more complex, but there is security through simplicity.
The down side, though, is that embedded systems have very little support for identifying and correcting security issues. Often, it’s best to have these on their own network.
A type of computer designed for deployment in an industrial or outdoor setting that can automate and monitor mechanical systems. An example of this would be a controller for opening/shutting a valve.
PLC firmware can be patched and reprogrammed to fix vulnerabilities, but they require a very tedious process with limited support. Furthermore, these usually have long intervals between patch releases, up to a year or more.
A processor that integrates the platform functionality of multiple logical controllers onto a single chip. These offer more compute power than PLCs, and space efficiency.
For embedded systems in critical applications, we have RTOSs. These operating systems prioritize deterministic execution of operations to ensure consistent response for time-critical tasks.
Embedded systems typically cannot tolerate reboots or crashes and must have response times that are predictable to within microsecond tolerances.
A processor that can be programmed to perform a specific function by a customer rather than at the time of manufacture, as opposed to the SoC being programmed by manufacturer.
End customer can configure the programming logic to run a specific application instead of using an ASIC (application-specific integrated circuit).
This is a communications network designed to implement an industrial control system rather than data networking. ITs cousin.
Industrial systems prioritize availability and integrity over confidentiality.
These are networks that manage embedded devices.
ICS is used for electrical power stations, water suppliers, health services, telecommunications, manufacturing, and defense needs.
Digital serial data communications used in operational technology networks to link PLCs. This facilitates the communication between all the embedded devices within a system.
Input and output controls on a PLC to allow a user to configure and monitor the system.
ICS manages the process automation by linking together PLCs using a fieldbus to make changes in the physical world (values, motors, etc…)
Software that aggregates and catalogs data from multiple sources within an industrial control system. When starting a job in OT, good to know where to find this as soon as you start the job.
A type of industrial control system that manages large-scale, multiple-site devices and equipment spread over geographic regions.
SCADA typically runs as software on ordinary computers to gather data from and manage plant devices and equipment with embedded PLCs.
This is the communications protocol used in operational technology networks.
TCP/IP is to IT as Modbus is to OT.
Modbus gives control servers and SCADA hosts the ability to query and change the configuration of each PLC.
Four key controls for mitigating vulnerabilities in specialized systems. Reference the NIST Special Publication 800–82
WARNING: Enumeration tools and vulnerability scanners can cause problems on Operational Technology Networks. Wireshark is usually used.
Systems used for building automation and physical access security.
Many system designs allow the monitoring to be accessible from the corporate data network or even directly from the Internet
Components and protocols that facilitate the centralized configuration and monitoring of mechanical and electrical systems within offices and data centers. Possible vulnerabilities for such systems include:
Denial of Service conditions could be caused by affecting building automation systems like HVAC.
Components and protocols that facilitate the centralized configuration and monitoring of security mechanisms within offices and data centers.
PACS can either be implemented as part of a building automation system or a separate system.
WARNING: PACS are often installed and maintained by an external supplier and are therefore omitted from risk and vulnerability assessments by analysts. Even though, maintained by an external supplier, don’t assume they have good security. In fact, it’s in your interest to assume they have bad security.
…and that wraps it up for facilities security.
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!