
Virtual Machines, Virtualization, and Using This Stuff for YOUR Own Personal Cyber Security
Since I recently learned of this thing, I think people who have never heard of a MAC address would gain the most from this post. Anyone who knows more than me (I’m sure that’s most people) will be bored by this.
Anyway, enough self-deprecation from me. Let’s get into it.
MAC stands for media access control. This is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. Other names for a MAC address include:
Basically, the MAC address is what identifies your computer or mobile device to the router that is serving the Wi-Fi. Routers also have MAC addresses.
Depending on who you are, you can use MAC address spoofing for good or for bad. Simply put, MAC address spoofing merely just means changing a MAC address.
For good, you can use this technique to reclaim some privacy. Because MAC addresses act as unique identifiers for Wi-Fi enabled devices, these addresses can be used to track your movements, whether by Starbucks for marketing purposes, creepy ex-lovers to follow you around or overbearing parents. To combat this, there are apps that you can use. Also, you can manually change your MAC address or use a MAC address randomizer. There’s a configuration you can set so that Windows will randomize your MAC address for you. It’s pretty easy. I’ll describe how to do that and check your MAC address via the command line terminal after I mention some of the bad things that someone can do with MAC address spoofing.
According to several sources, MAC address spoofing is very easy to do. The authors of one academic article describe spoofing as “changing the MAC address of a wireless device that exists in a specific wireless network using off-the-shelf equipment.”
Huh?! “…off-the-shelf equipment.” Sounds very accessible.
Then what? What types of “attacks” can one do after changing a MAC address? From the same article, the authors go on to describe the various attacks as such:
“[This] is a serious threat to wireless networks. For instance, an attacker can spoof the MAC address of a productive access point (AP) in WLAN-infrastructure mode and replace or coexist with that AP to eavesdrop on the wireless traffic or act as a man-in-the-middle (this attack is known as the evil twin attack). In addition, the attacker can flood the network with numerous requests using random MAC addresses to exhaust the network resources. This attack is known as resource depletion.”
Translation: there are several avenues of attack via MAC address spoofing.
So, why should you know about this? I’ve vaguely alluded to why already, but more directly, below are a few specific reasons.
Checking your MAC address:
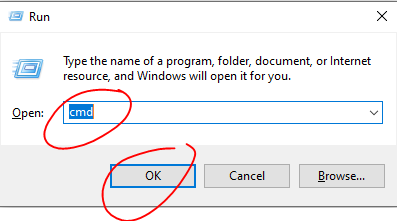
ipconfig /all(I believe the equivalent of this for linux and apple devices is ifconfig) and press enter.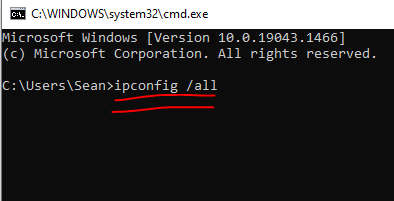
Configuring your computer to use randomized MAC addresses:
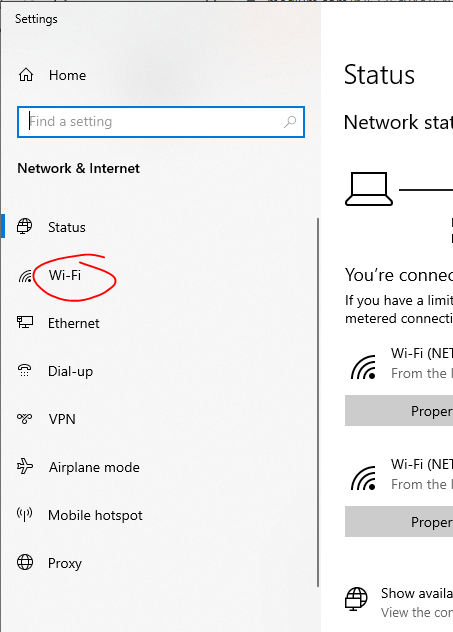
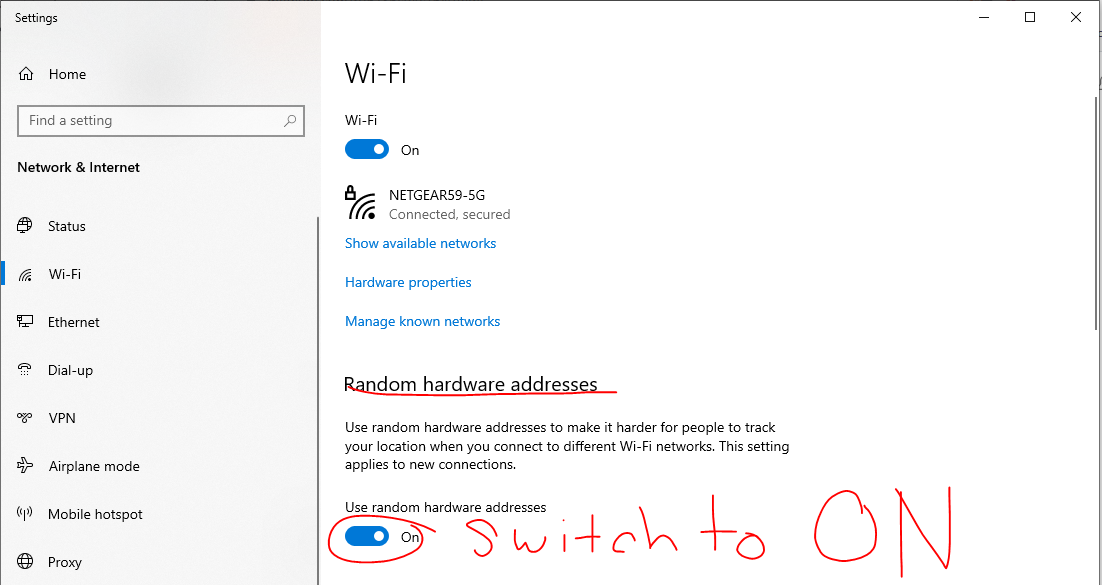
All this can seem overwhelming. At least it does for me oftentimes. However, the way I’ve overcome my overwhelm and gain peace-of-mind is by learning. What I know so far is probably spotty with lots of gaps of knowledge, but over time I’m filling in those gaps. Hopefully, by sharing what I learn, others can attain some peace-of-mind, as well.
A bientot, mes amis!
Work Cited:
A New MAC Address Spoofing Detection Technique Based on Random Forests
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!