
How to Manually Change Your MAC Address and a Teeny, Tiny, Simple, Little Python Algorithm to Do It for You on Linux or Apple Operating Systems
Don’t worry, nothing illegal here.. Let me be honest really quick, though. I’ve recently become paranoid for my own “digital well-being” so I started researching ways to protect myself digitally. With that said, what I lack in experience is certainly made up by thorough research, followed by repeated application, and maybe a dumb analogy using a movie reference. Anyway, enough banter from me.
Below will explain virtualization, virtual machines, and how these are applied, for good and for bad. I will try to explain this as if talking to a 4 year-old. Then again, 4 year-olds probably know more about this stuff than I do in this day and age. Anyway, the steps on how to install and use this stuff on a Windows 10 OS will be described at the end.
Basically, in imaginary terms, a box is created on your computer. This box is completely isolated from your computer’s other functions, but you can use this box to run a completely separate computer inside of your computer.
For example, say we have a Windows computer but we want to try out a Mac OS. Well, from my basic understanding, one can have this box on their computer and simply download the Mac OS to run inside of this box. With this set-up, a person could switch between using the actual machine (Windows) and the virtual machine (Mac) running inside this mysterious box (this box will be explained below).
Wikipedia puts it simply and states that “a virtual machine (VM) is the virtualization/emulation of a computer system.” This allows a Windows operating system to be run on a Mac and vice versa.
One could even do nested virtualization, where a virtual machine runs inside of a virtual machine inside of an actual machine. Like that movie Inception, with the dreams inside of dreams and so on…
For a more technical explanation, please refer to the Wikipedia links below:
Depending on who you are, this can be used for good or for bad. Let’s see how people can use this technology to keep themselves safe or carry out nefarious activities:
Enable Virtualization. This is not a default setting for Windows, like it is for Mac. However, it is crucial to enable this before starting. This won’t be covered but here are a few guides to try:
Download 7zip. This is an uncompressing software that we’ll need because the virtual machine download will be compressed as a .7z file and will need to be uncompressed before being able to run it.
Everything is downloaded and now to start using this stuff:
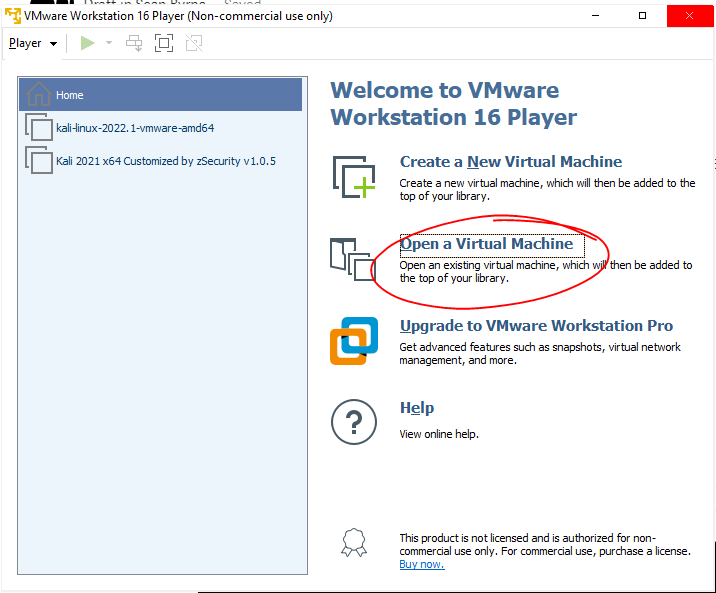
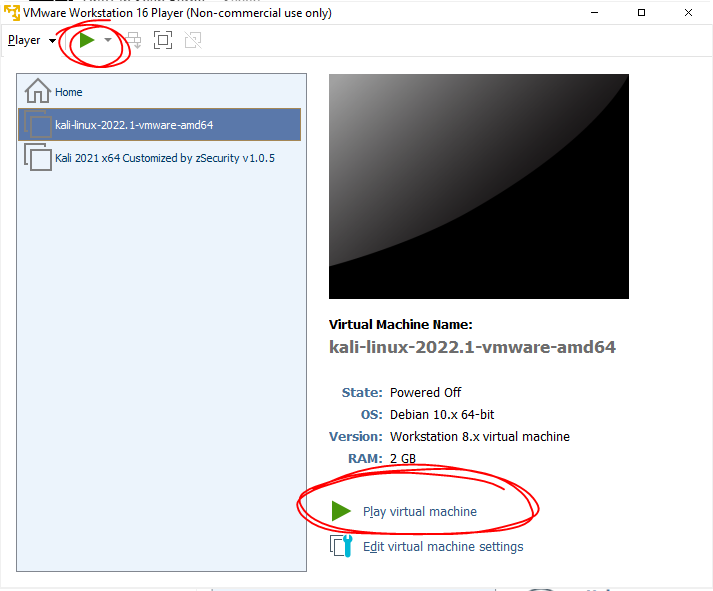
3. Press the green Play button
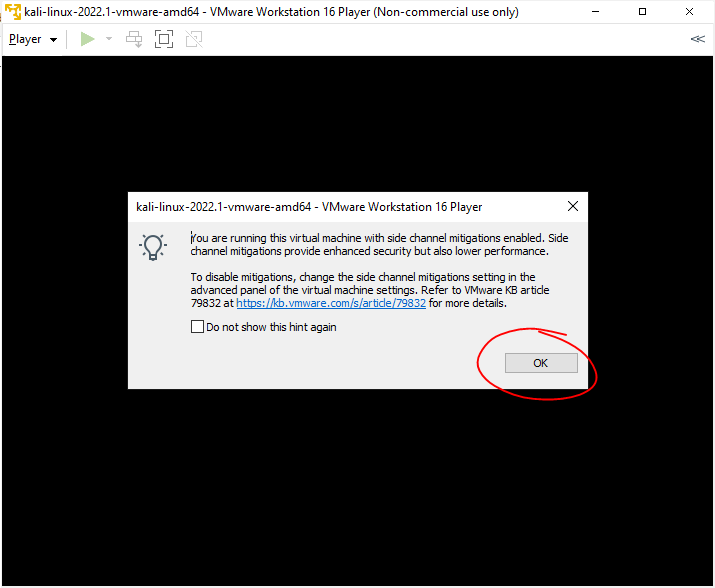
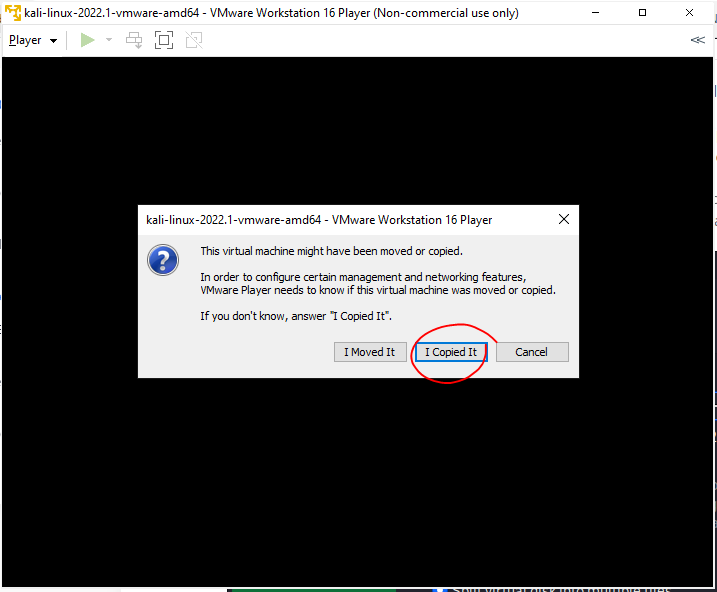
4. Click “OK” and “I Copied It”
5. Login with the default credentials

… and voila! A computer within a computer:
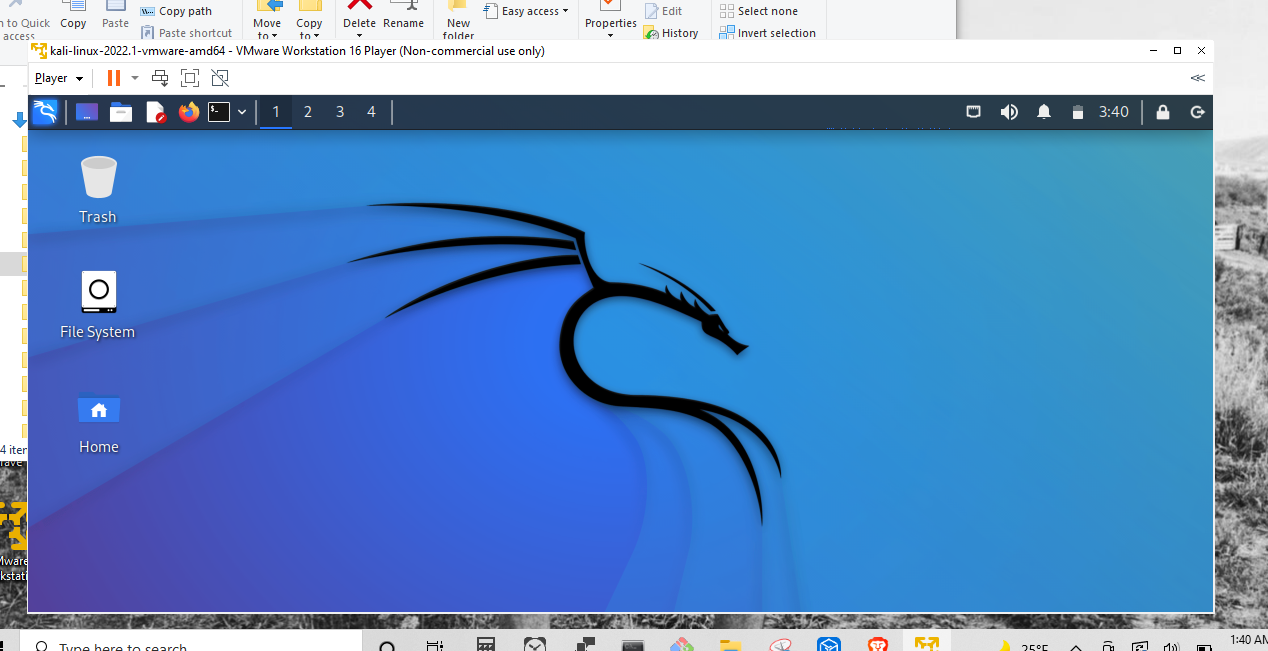
With this set up, you can do anything you could on a physical computer. For example you can browse the internet but now there will be an added layer of security. Basically, if anything goes wrong in the virtual machine, it will be isolated from the actual machine.
As Porky Pig would say, “That’s all folks!”
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!