
Hardening
There’s something really simple to remember regarding the physical aspect of cybersecurity:
if an attacker can physically touch your devices, they can own your devices
With that in mind, keeping unauthorized persons away from physical reach of your devices is imperative to overall cybersecurity. An organization could have all the best cybersecurity software and hardware, but that won’t count for anything if some asshole can simply walk up to a computer and install a virus from a USB drive.
Simple concept, with some simple solutions. Fences, security guards, sign-in sheets, road blocks. Pretty obvious, you probably could have guessed those.
Surveillance is another common security measure. Ideally, organizations should use closed circuit TV (CCTV), because wireless security cameras can be easily hacked. Also, if there’s room in the budget, best to splurge for the cameras with Pan, Tilt, Zoom (PTZ).
To get an idea of how many cameras a facility needs, best practice is to have a camera for every entrance and exit. Other types of surveillance equipment include infrared and ultrasonic.
Another obvious, but maybe overlooked, solution includes door locks. These are important because they protect an organization’s machines when perimeter defenses have failed… thanks for trying Paul Blart.

Anyway, locks come in many different flavors. There are the basic key locks, but they can get more high-tech, which include pin number locks, wireless signal locks, or biometric locks. The handy thing about these electronic locks is that they can have a log of who has used the lock. This is handy for pinpointing perpetrators or identifying compromised individuals.
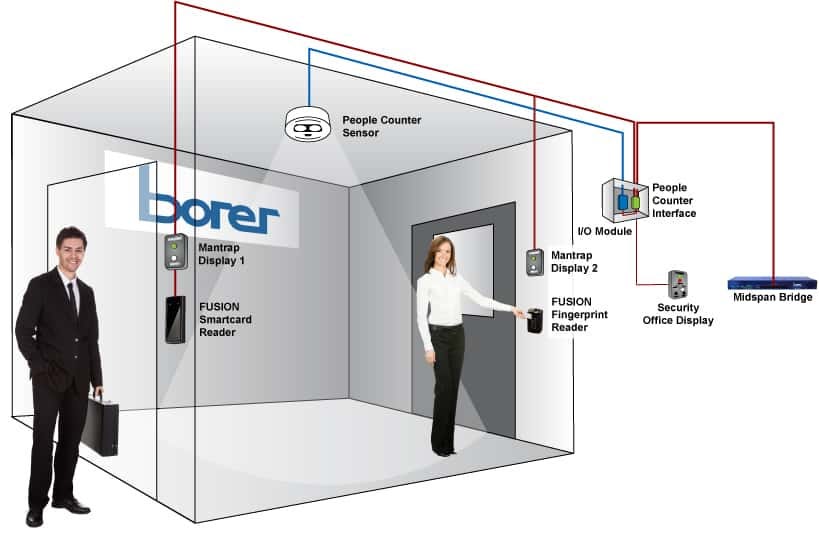
If you’re feeling kinky and you want to upgrade your perimeter security, then you might want a mantrap. Simply stated, this is an area between two doorways that holds people until they are identified and authenticated.
BONUS TIP: set beartraps & booby traps within the mantrap for maximal effect.
…just kidding, do not take that advice.
These are becoming more common and provide an effective security measure. They rely on the physical characteristics of a person to identify them.
Authentication can occur in many ways and there are 5 categories. Depending on the level of security needed, one or all can be incorporated. We can authenticate a person with:
So, biometrics authenticate a person by using a unique physical characteristic of a person’s body, like their retinas or fingerprint
While effective, some biometric systems can require some ‘tuning’ and we need to consider the False Acceptance Rate (FAR) and the False Rejection Rate (FRR). The FAR tells us the rate a system authenticates a user as authorized or valid when they should not have been granted access to the system. In contrast, the FRR gives us the rate that a system denies a user as authorized or valid when they should have been granted access to the system.
If you’re shopping around for biometric systems then a useful metric to compare systems is the Crossover Error Rate (CER). This is a measure of the effectiveness of a biometric system. So there you go… time to shop till you drop!
That’s all I have to write about physical security… have fun getting physical!
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!