
DNS Spoofing
We’ll be covering methods of security pertaining to the ‘workstation and laptop level.’ Pardon the crude humor above btw… I just had to get it out of me. I’ll be serious for the rest of the article…maybe, maybe not ;p
But really, I do feel this is important. More importantly, I hope people can use this information to keep themselves safer in the digital world!
There are many types of firewalls, but we’ll specifically cover personal firewalls since that’s more relevant since the majority of us are individuals. They protect a single computer from unwanted internet traffic. Personal firewalls are also known as host-based firewalls.
Fortunately, for all of us, each major OS has their own built-in firewall protection. These are quite effective too. Many people recommend these over purchasing a third party software, but I’ll leave that for you to decide. I personally use McAfee, but upon learning more I think I’m going to cancel that and try the Windows Defender Firewall w/ Advanced Security. This can be accessed by opening the command prompt and then typing:
wf.msc
Then another window will open and there you’ll have access to do more advanced firewall configurations, like Inbound & Outbound Rules. You can also access just the basic configurations via the Control Panel. Click on ‘System and Security’ and then you’ll see it in the next window. Refer to the screenshot and caption below.
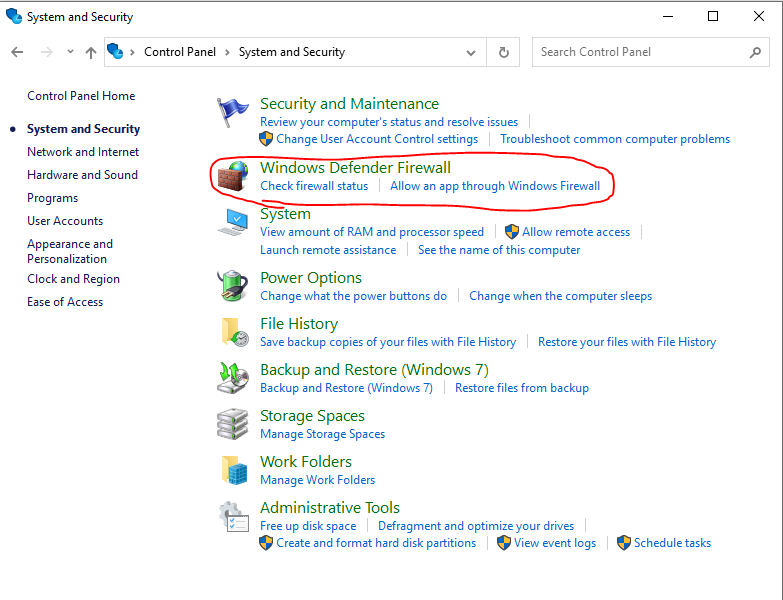
Macs have their own built-in firewall protection as well. However, that one is called Packet Filter (PF for short). It’s called this because that’s basically the function of a firewall — filtering out bad packets. This is also accessed through a command prompt, but I believe there is a GUI option for this on Mac. Anyway, this was called IPFW on old versions of Mac.
Lastly Linux has one too. It is called iptables and type that into the command prompt to set configurations.
This can be a device or software that monitors a system or network and analyzes the data passing through it in order to identify an incident or attack.
There are two different types of IDSs. Host-based IDS (a.k.a. HIDS) and these monitor the packets coming to an individual computer and come in the form of a software for download. One thing to note is that some people don’t like these because they have high CPU demands. Then there’s Network-based IDS (a.k.a. NIDS), which can come as a piece of hardware or for download as a software. These are installed to monitor intrusions at the network level. Ideally, for an organization, it’s best to implement both.
Now what parameters are these IDSs using to detect intrusions? They go by three different methods of detection. Those being:
Signature-based — a specific string of bytes triggers an alert
Policy-based — relies on specific declaration of the security policy (for example, ‘No Telnet Authorized’)
Anomaly-based — analyzes the current traffic against an established baseline and triggers an alert if outside the statistical average
Finally these alerts have four categories:
True positive — malicious activity is identified as an attack — good
False positive — legitimate activity is identified as an attack — bad
True negative — legitimate activity is identified as legitimate traffic — good
False negative — malicious activity is identified as legitimate traffic — bad
It’s important to note that IDSs can only alert and log suspicious activity. It can’t stop executables. To stop those, one would use an IPS, or Intrusion Protection System. However, IDSs are important for monitoring and more specifically HIDS logs can be used to recreate the events after an attack has occurred. For this reason it is crucial to have these logs sent to an external system log server to be protected from being modified by the attacker.
Malicious attackers will purchase ads (pay-per-click format) through various underground channels and these ads promote their nefarious doings. Thankfully, most web-browsers have the ability to block JavaScript generated pop-ups. Of course, there are many legitimate sites that use pop-ups like online school portals, or some payment processing. For that reason, users also have the option to enable pop-ups for certain sites.
Content Filters go a step further and will block external files containing JavaScript, images, or web pages from loading in a browser. AdBlocker is a free, open-source content filter that comes highly recommended. On that note, to further ensure pop-up blockers work effectively, regularly update browsers and their extensions.
This security measure monitors the data of a system while in use, in transit, or at rest. It comes as hardware or software. There are four different types:
Endpoint DLP System — software-based client that monitors the data in use on a computer and con stop a file transfer or alert an admin of the occurrence; data in use
Network DLP System — Software or hardware-based solution that is installed on the perimeter of the network to detect data in transit, focuses on outbound data; data in transit
Storage DLP System — software installed on servers in the datacenter to inspect the data at rest; for example an alert would be set off if terabytes of data were downloaded at 2 a.m.
Cloud DLP System — cloud software as a service that protects data being stored in cloud services; data at rest
BIOS stands for Basic Input Output System. It is very low-level, but it is firmware that provides the computer instructions for how to accept input and send output. It is handy to think of the BIOS as the ‘middle-man’ that goes between the OS and the hardware (the computer’s motherboard) on which the OS runs. Simply stated the motherboard communicates via the BIOS to the OS and the keyboard, and mouse, etc... In recent times, however, UEFI (Unified Extensible Firmware Interface) has become preferred by manufactures. UEFI is basically the same thing but more updated than BIOS, so in this context we can refer to them interchangeably.
…But how do we secure the BIOS?! Well here are the steps, but very simply stated:
We all know removable media devices come in many different formats, like floppy disks, CDs, external hard drives, thumb drives, and so on… Well they need to be secured as well. Fortunately these devices are easily secured with encryption.
Going the other way, we also need to secure ourselves from removable media devices. We do this by placing technical limitations on a system in regards to the utilization of USB storage devices and other removable media. Examples of this would be ‘denying read access on a USB’ or ‘denying write access to CDs.’ This can be done by creating administrative controls such as policies.
Other network based storage system exist as well and they are known as Network Attached Storage (NAS) and Storage Area Network (SAN). NAS devices connect directly to the network and they are useful because they often implement RAID arrays to ensure high availability. A SAN is a network that is specifically designed to perform block storage functions that may consist of NAS devices. So, there are three best practices in securing these storage systems. They consist of using data encryption, proper authentication and log the access to the NAS or SAN.
This type of encryption scrambles the data on your hard drive into unreadable information. Highly recommended when traveling with any type of wireless device, like your cell phone and laptop.
To do this, we have things like Self-Encrypting Drives (SED). This type of storage device performs whole disc encryption by using embedded hardware. These are very fast, but very expensive. A more budget-friendly solution would be encryption software. Two of the most commonly used ones are FileVault and BitLocker.
BitLocker for example uses the Trusted Platform Module (TPM) This is a chip residing on the motherboard that contains an encryption key. If the motherboard doesn’t have a TPM, then the user can use an external USB drive as a key.
In addition to using the TPM, BitLocker and FileVault will use Advanced Encryption Standard. This is symmetric key encryption that supports 128-bit and 256-bit keys.
While encryption does add security, it does lower performance by sacrificing speed. This provides a great example of the perpetual struggle between ‘convenience and security’ that exist within realm of InfoSec. To avoid sacrificing speed, however, we can encrypt at the file level instead of whole disc encryption.
Another encryption tool is a Hardware Security Module (HSM). This is a physical device that acts a secure cryptoprocessor during the encryption process. This is a means of speeding up encryption, but it too is expensive. Most companies still use software based encryption.
I’m sure many people reading this know what an endpoint is. For those who don’t, though, it is simply any device we might use to connect to our network, like our laptops and cellphones, etc… Anyway, ‘endpoint analysis’ refers to the monitoring, logging, and analyzing of our endpoints. This is basically an umbrella term for security tools applied to our devices and not on networks. So it’ll include several terms covered earlier.
Cyber security analysts use endpoint analysis tools to identify behavioral anomalies. Then they’ll identify the techniques used by malware to conduct privilege escalations and become persistent on a host.
Fortunately several tools exist for us to use. Some of which many of us are already aware.
Anti-virus(AV) — we all know this one right? Well under the context of Endpoint Analysis it is software capable of detecting and removing virus infections and (in most cases) other types of malware such as worms, Trojans, rootkits, adware, spyware, password crackers, network mappers, DoS tools, and others…
Host-based IDS/IPS (HIDS/HIPS) — remember these? these monitor a computer system for unexpected behavior or drastic changes to the system’s state on an endpoint
Endpoint Protection Platform (EPP) — these are like a swiss army of security tools. They are a software agent and monitoring system that perform multiple security tasks such anti-virus, IDS/HPS/ firewall, DLP, and file encryption.
To compare the various EPPs available on the market, the industry refers to “Gartner Magic Quadrant,” which looks like this:
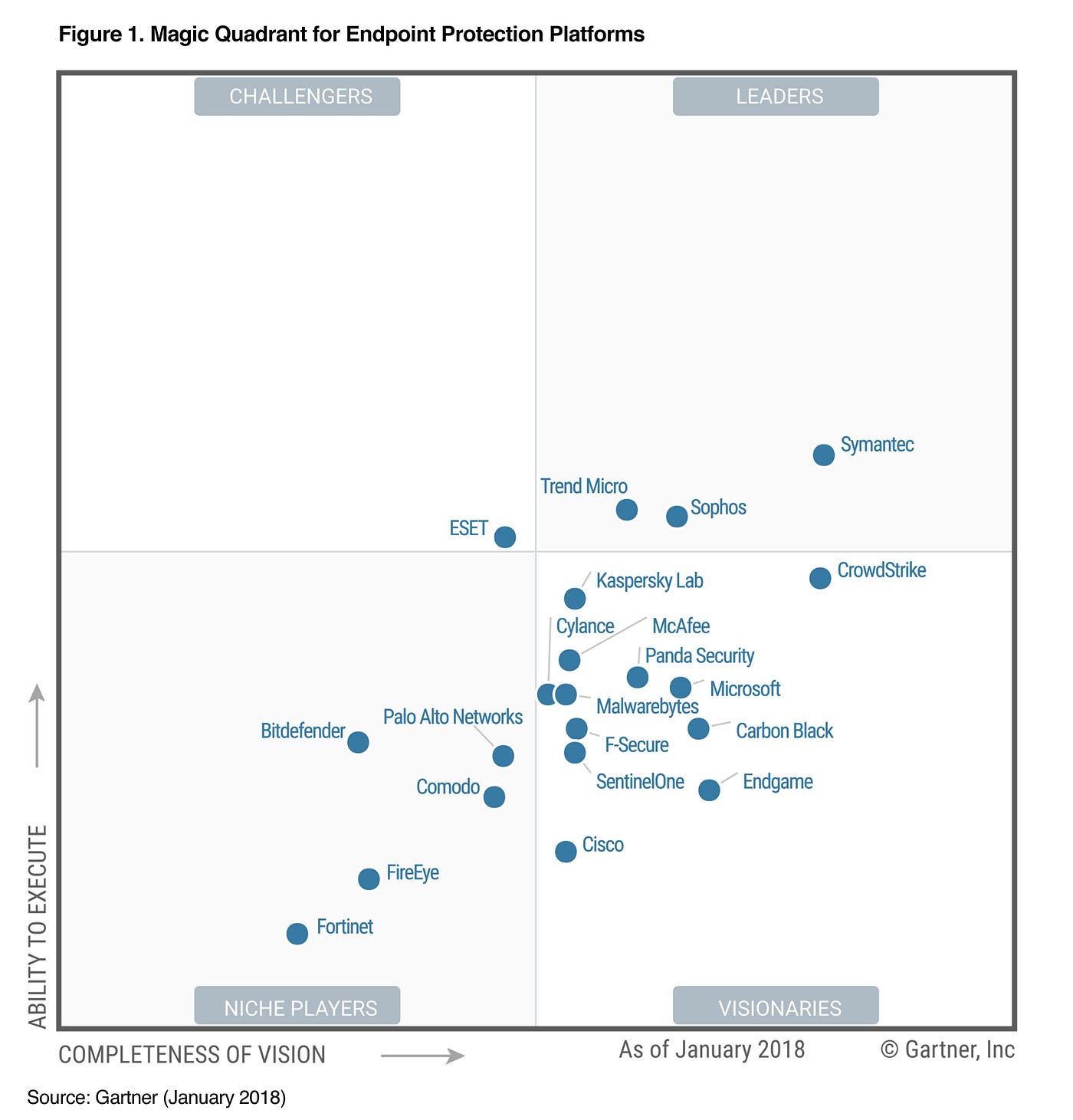
Don’t use the above quadrant as reference because it is out-of-date, but to get the up-to-date quadrant one must be a client of Gartner’s, apparently.
Endpoint Detection and Response (EDR) —this is software agent that collects system data and logs for analysis by a monitoring system to provide early detection of threat; it focuses on the behavioral analysis of computer processes.
User and Entity Behavior Analytics (UEBA) — this is a system that can provide automated identification of suspicious activity by user accounts and computer hosts. These need lots of data to process, because they are heavily dependent on advanced computing techniques like AI and machine learning. Check out Splunk and Microsoft Advanced Threat Analysis.
If you enjoyed reading this article, support my writing by signing up for a Medium subscription.
Medium is a writing platform where writers from all over the world showcase their writing, covering any topic you can think of.
With a subscription you'll have unlimited access to all these writers and email notifications for my newly posted articles.
...but never fear, if you really enjoy my cybersecurity articles, then they will always be available here to read for free, for you!